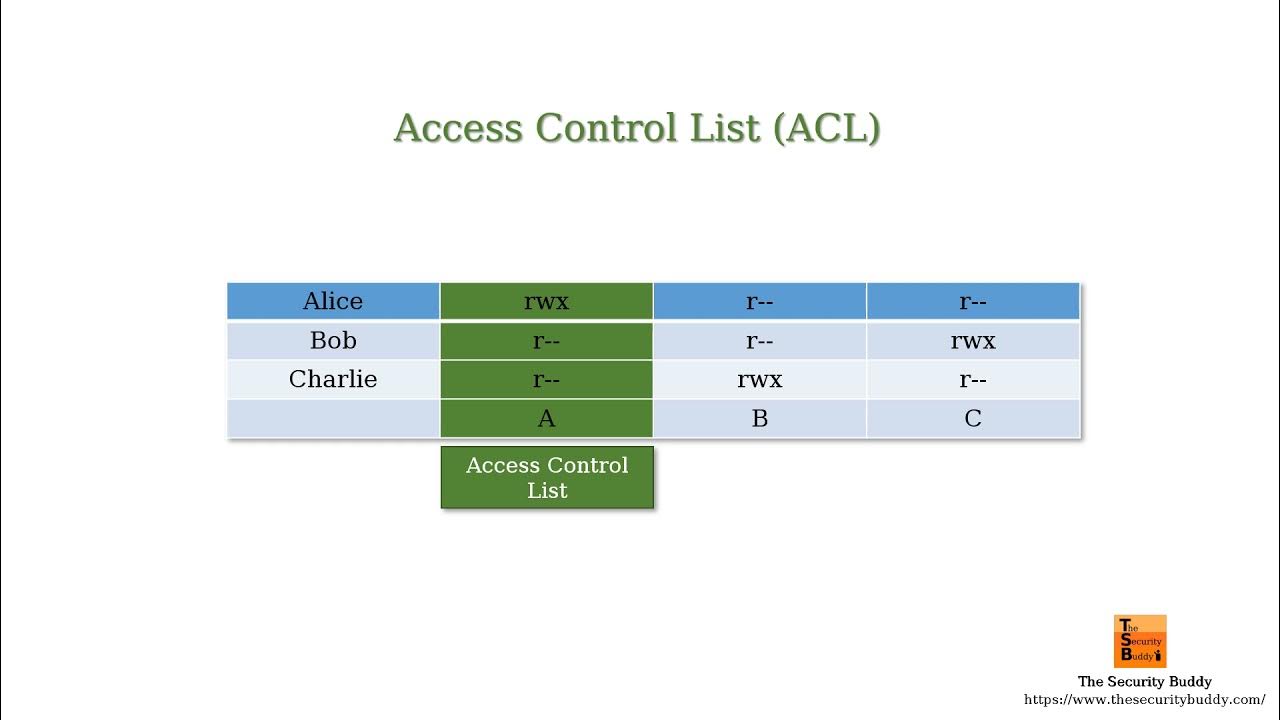
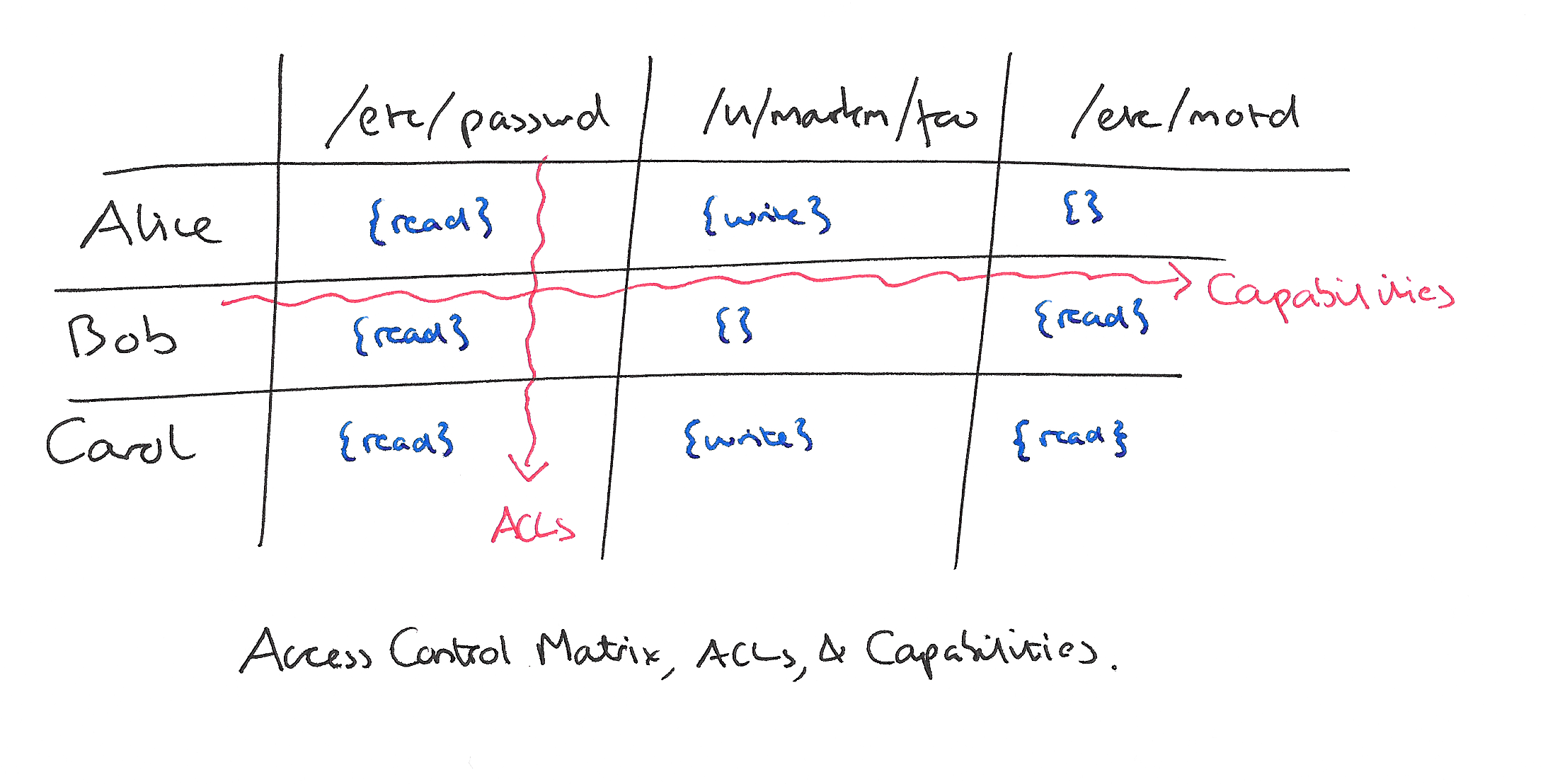
A capability-based security approach to manage access control in the Internet of Things - ScienceDirect

Capability-Based Access Control with ECC Key Management for the M2M Local Cloud Platform | SpringerLink
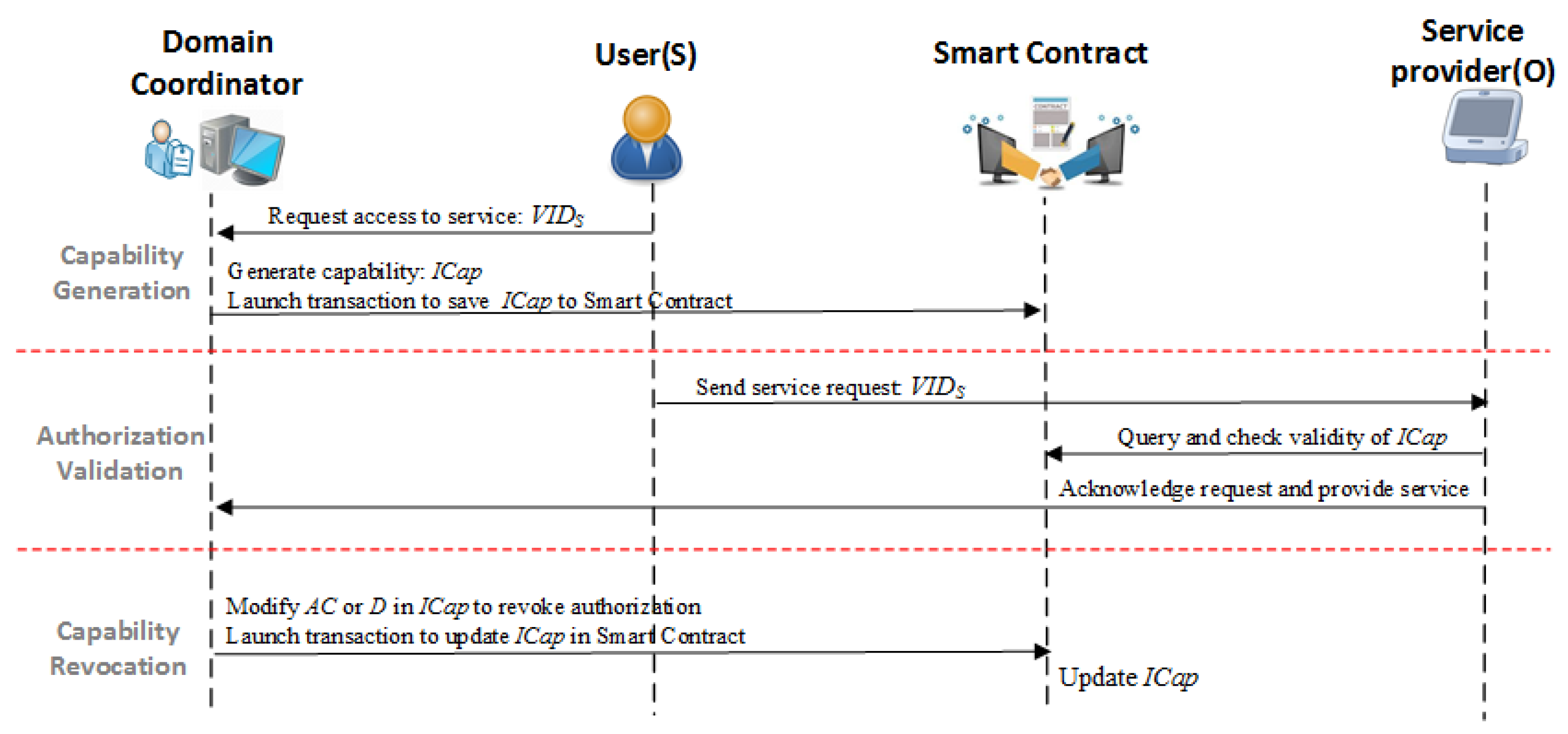
Computers | Free Full-Text | BlendCAC: A Smart Contract Enabled Decentralized Capability-Based Access Control Mechanism for the IoT
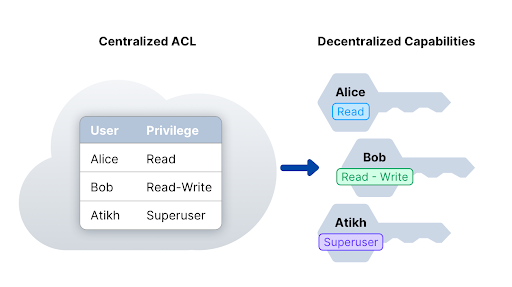
Capability-based security — enabling secure access control in the decentralized cloud | by Kevin Leffew | Medium

A capability-based security approach to manage access control in the Internet of Things - ScienceDirect

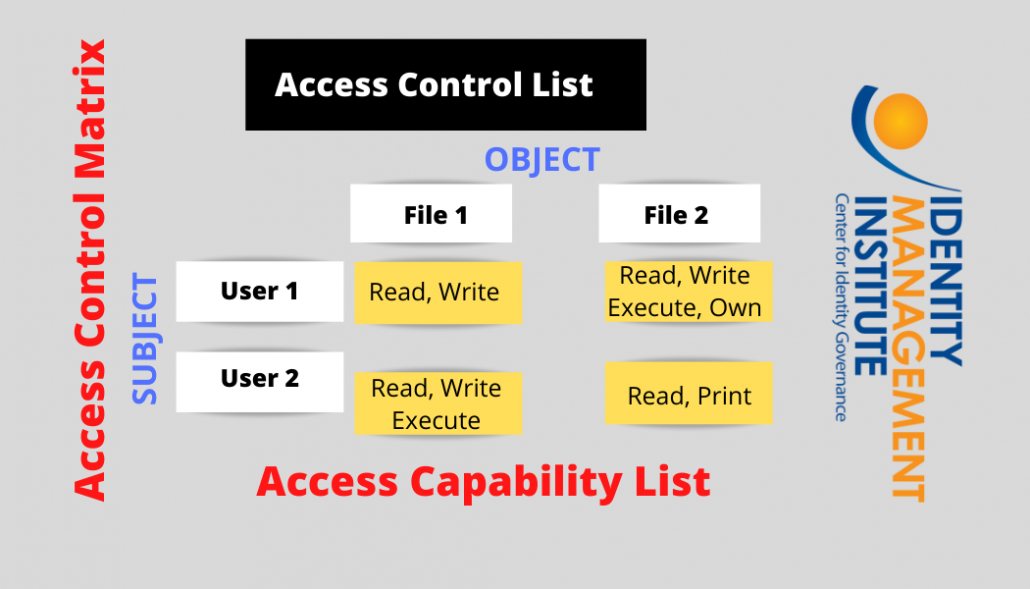
PDF) Managing Access Control for Things: a Capability Based Approach | Salvatore Piccione - Academia.edu

A capability-based security approach to manage access control in the Internet of Things | Semantic Scholar

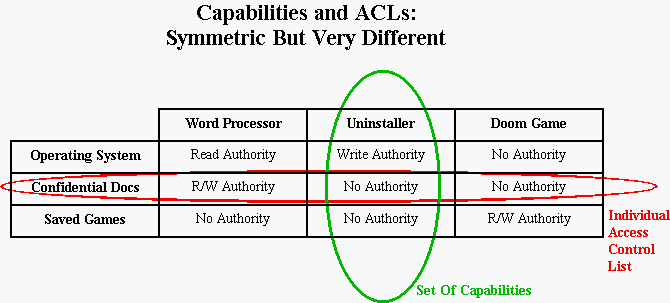
provides examples of potential usage of capability based authorization... | Download Scientific Diagram